- TOP
- Cutting-edge Research and Social Contribution
- Cutting-edge Research
- Almost zero processing load: Solving security issues in the IoT era with SAS-L, the ultimate authentication method

Almost zero processing load: Solving security issues in the IoT era with SAS-L, the ultimate authentication method

SHIMIZU AkihiroSHIMIZU Akihiro
- Specialized field
Information security, Information networks
Invention of the FEAL high-speed encryption system, a significant impact on cryptographic research
The Internet has become a social infrastructure that is indispensable in people's lives, a lifeline ranking with water and electricity. However, while users can now enjoy a variety of Internet services, they are constantly exposed to security threats. In order to protect data from unauthorized manipulation by malicious parties, and to maintain the security of the system, it is important to establish a simple mechanism for distributing content safely at high speed.
Prof. Shimizu conducts research towards the development of encryption and authentication methods that can be adapted to any environment, from computers with high processing power to small devices with limited memory and processing capacity. He is a top researcher in the information security field, and he has invented many encryption and authentication methods. His creations are the strongest, the fastest, and the lightest in the world.
Encryption and authentication are the most fundamental elemental technologies for security work. A system that could adapt to any environment would greatly expand the range of possible security technologies and IT services.
Prof. Shimizu says, "I am thinking of a system in which goods in stores such as convenience stores have IC tags attached, incorporating the encryption and authentication method that I developed, so that customers can complete their payment just by passing through an unmanned cash register, holding up each item they have chosen. That system would be able to transmit and authenticate over short distances, and all communication data could be encrypted, allowing the transaction to be settled securely. This is just an example; but in any system that uses these cutting-edge technologies, the key technologies are cryptography and authentication.''
Originally a researcher at NTT (Nippon Telegraph and Telephone Corporation), Prof. Shimizu devised FEAL (Fast Data Encipherment Algorithm) in 1985. FEAL, a lightweight program with high processing speed, boasts the world's highest level of encryption. It was a remarkable accomplishment for Prof. Shimizu, then in his fourth year with the company. FEAL, which has performance far superior to that of the US-born encryption system DES (formerly the global standard), has been adopted for use in credit card payment terminals, mobile phones and IC cards.
Prof. Shimizu explains, "At that time, when IC cards were beginning to be put to practical use, the memory capacity of the card was only 8 KB. The program of DES required 3 KB, so it was difficult to add the necessary data and an encryption mechanism. I was mandated by my company to create a cryptographic system that was lightweight, yet highly secure, with high processing speed."
FEAL successfully reduced the program memory requirement to 1/6, with the same strength as DES. This cryptographic technology, created in the early days of the Internet, was regarded as one of NTT's three major inventions. It has had a major impact on the development of cryptographic research ever since.
SAS-2: The world's fastest authentication method, realizing high-speed, secure encrypted communication
In an information communication system, when the authentication side (a server) authenticates a user, it commonly uses a password authentication method that requires the user to input a password and authenticates the user if the inputted password is valid. In particular, in the Internet, which is widely used as a social infrastructure, a "one-time password authentication method" is used, in which the password is thrown away after a single authentication in order to prevent the password from leaking to the network, with the risk of it being stolen. This method is used for user authentication in scenarios such as logging in to cloud services and application services: a new encryption key is generated every time, based on information updated during each authentication, thus enabling secure encrypted communication. Further, if the processing load of the authentication is small, it is possible to achieve encryption communication using a different encryption key for each information communication unit (e.g., a packet) in the communication between the server and the user.
The pioneer one-time password authentication method suitable for Internet use is S/Key, developed in the United States. Prof. Shimizu recalls, "When I was at NTT, S/Key was the only one-time password authentication method available on the Internet." He developed SAS (Simple And Secure password authentication protocol) in 2000 to improve the speed performance of S/Key, and in 2002 he developed SAS-2, with further improvements.
SAS-2 is characterized by its small processing load for authentication between server and user, and its ability to update authentication information at high speed.
"Among the one-time password authentication methods that change the password each time they are authenticated, this is the fastest in the world; there is still no faster method. If you use SAS-2, secure encrypted communication using keys can be realized without difficulty, even using a different key for each packet.''
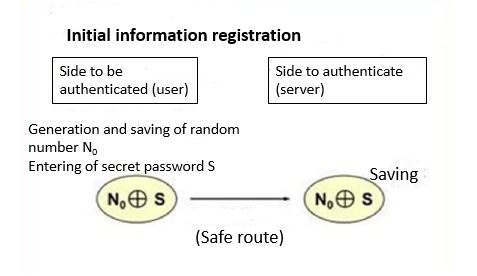
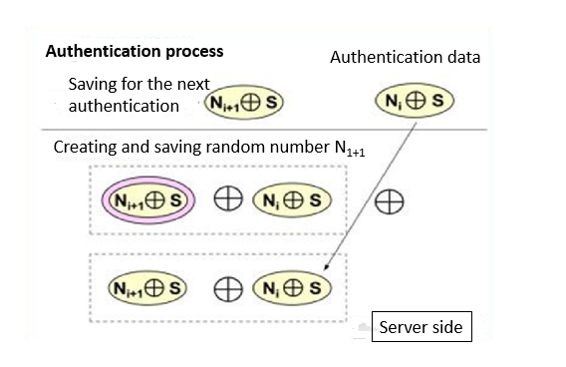
(Overview of the SAS-2 process)
This revolutionary authentication method eventually attracted the attention of companies, which opened the way to practical implementation. Initially, a software/hardware development company integrated SAS-2 into a wireless LAN and developed a wireless LAN product with high security and high-speed communication. Since the product had the advantage of easy setup and low cost, it was installed in the main branch of Shikoku Bank, Ltd., and was also adopted by a general contractor as an essential wireless LAN communication for installation in new buildings. Now, SAS-2 is also used for authentication in the user login system in a medical application service provided by Fujitsu Limited.
Prof. Shimizu has been recognized for his achievements in the development of FEAL and SAS-2. He has received a number of prestigious awards including the National Invention Commendation (Minister of International Trade and Industry Award) in 1997, the Minister of Education, Culture, Sports, Science and Technology Award in 2007 and the Kochi Prefecture Distinguished Service Award in 2008.
Prof. Shimizu has been involved in research on encryption and authentication methods since the dawn of the Internet. Needless to say, the encryption and authentication method invented by Prof. Shimizu has played a major role in the rapid spread of IoT services.
SAS-L, a one-time password authentication method with a wide range of IoT applications
With the rapid spread of the Internet of Things (IoT), everything is connected to the Internet, and new business and services are created using the data obtained. As the IoT market is expected to grow rapidly in the future, IoT security measures have become a major issue. Security measures are now applied both high-performance IoT devices such as home appliances, connected cars and smart grids, and small, low-spec IoT devices such as agricultural humidity sensors and IC tags. This means that there is a need for a different approach to information technology.
Prof. Shimizu explains, "To connect IoT devices to the Internet and to use Internet services, mutual authentication is required between the server and the user (IoT device), but for data exchanges like that, it's essential to have technology that can perform high-speed authentication and key distribution to ensure that no third party can enter. That kind of authentication and distribution is no problem for devices with sufficient processing capacity, but it is very difficult for small devices with low processing power to process such complicated cryptographic communication."
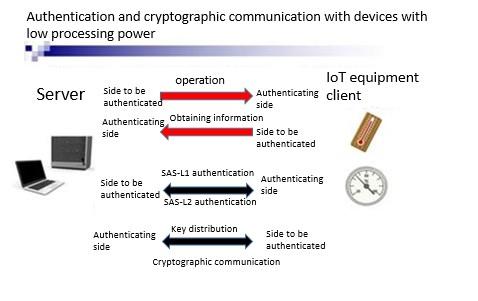
For IoT devices with high processing power, SAS-2 can be used, since it can easily realize high-speed authentication and encryption key distribution. However, low-spec small IoT devices require an authentication method with a much smaller processing load.
In 2018, Prof. Shimizu devised SAS-L, a revolutionary authentication method that immediately solves those IoT security issues. He says proudly, "This is a great invention which may shake the world." What are the features of SAS-L?
The speed performance of a one-time password authentication method can be evaluated as the number of one-way conversions with the largest processing load. A single one-way conversion requires as much processing as hundreds of ordinary operations such as addition and subtraction; S/Key uses one-way conversion more than 100 times in each communication. On the other hand, SAS-2 has successfully achieved authentication using one-way conversion only twice on the user side and once on the server side.
"To realize advanced cryptographic communication in the IoT security field, where low-spec small devices are also increasing in number, it's important to find a way to reduce the number of times one-way conversion is applied on the user side (i.e. in an IoT device)."
To solve that problem, Prof. Shimizu successfully created SAS-L1, which requires one-way conversion only once on the user side and zero times on the server side. In addition, he proposed replacing the one-way conversion function used in SAS-2 with a simple operation with a small processing load--where the user side did not use the one-way conversion function. This led to the successful development of SAS-L2, achieving authentication by means of a simple operation consisting of two EXCLUSIVE-OR operations and three additions.
Prof. Shimizu is pleased about those results. He says, "We have achieved zero user one-way conversions, something that has never been done before." Thanks to SAS-L2, mutual authentication can be achieved with almost no processing load, so advanced security functions can be implemented in a wide range of IoT domains.
He adds, "That's not all. By adding one more EXCLUSIVE-OR operation to SAS-L2, in addition to authentication, we can add high-speed 64-bit encryption communication (Burnam cipher). In terms of processing, three EXCLUSIVE-OR operations and three additions make it possible to perform everything from authentication to high-speed, complex cryptographic communication, realizing a long-standing dream of being able to protect against external attacks. With the development of IoT, this is now surely the most indispensable foundation technology.''
In cryptography and authentication, it's important to reduce the processing load and expand the range of applications, while maintaining the same security strength as that of the conventional method. Prof. Shimizu has been developing cryptography and authentication technology for more than 30 years. He has the soul of a true researcher, constantly looking for a problem to be solved.
"I started researching cryptography and authentication when I was with NTT, and when the results I developed were delivered to the world, many people understood their necessity and used them. Those results became useful for people. Even now, I am over 60, but I can still come up with new formulas. It's really exciting. I think this is a happy life."
Prof. Shimizu says this is his last development of new foundation technology. In the future he will focus on applied research using the encryption and authentication methods that he has devised. His creation, a unique and powerful encryption / authentication method, is poised to significantly change our lives.


